There’s been a significant security leak about SSL, called Heart Bleed Bug, which affects about 2/3 of the servers’ internet.
Apache and Nginx, two primary open-source web servers, have a combined market share of over 66% (Netcraft’s April 2014 Web Server Survey). They are the primary users of OpenSSL.
If you knew how to make $1200 a month online, from the comfort of your home, would you do the work?
…Well THIS is your chance
It’s FREE to get started, too (no credit card required). You’ll like that part…
1. Why is Heartbleed Bug So Serious?
The problem is that it allows stealing information that is protected by SSL/TLS encryption. SSL/TLS protects email, instant messaging, web, etc. Heartbleed bug makes it possible to steal protected data such as usernames and passwords and emails, instant messages, business communication, etc.
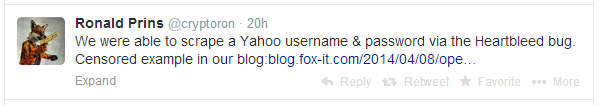
Ronald Prins of security firm Fox-IT tested the bug and wrote about it on Twitter:
He said that he ran the bug for 5 minutes and got 200 Yahoo usernames and passwords. Yahoo has already fixed the primary vulnerability on its leading websites (The Epoch Times), but I just wanted to give you an example of what the Heartbleed can do.
2. Why is Heartbleed Bug unique?
Other bugs just come and go, and each next version fixes them, so not much problem with them. However, the Heartbleed bug leaves a vast amount of private data exposed to the Internet for an extended period. “As long as the vulnerable version of OpenSSL is in use, it can be abused,” the website states. To read a more detailed review about Heartbleed Bug, visit Heartbleed.com.
3. Protect Yourself.
Open your browser settings and turn on the function that revokes any SSL certificates that you may have. When a certificate is issued to a secure website, this certificate contains data that allows your browser to validate that the certificate was not issued in error or has been compromised. In other words, it is checking if the certificate has been revoked by the company that issued the certificate.
3.1. Google Chrome:
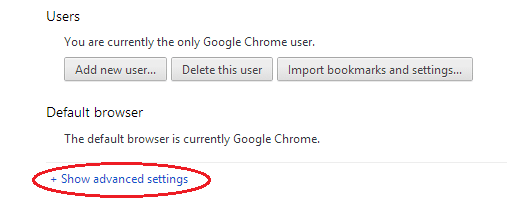
Open Settings of your browser and scroll down until you find +Show advanced settings.
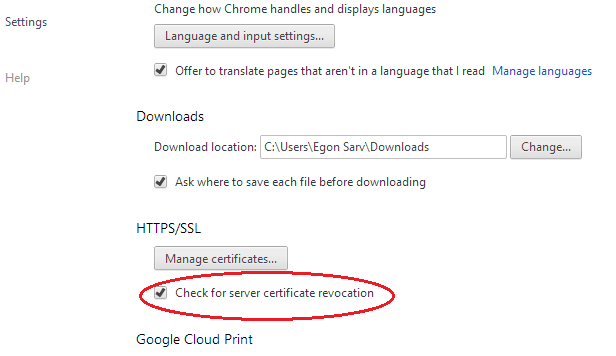
Open Advanced Settings and scroll down until you see HTTPS/SSL subtitle. Under it, check the box “Check for server certification revocation.”
3.2. Firefox
For more information, visit Mozilla: Using Certificates.
3.3. Safari
Bring up Keychain Access and go to Preferences. (If you can’t find it, search „Keychain“ using the command-space bar). Now hold down the Option Key and check„Require for all certificates.”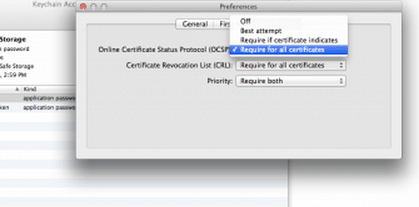
3.4. WordPress
There is a new security update available (08.apr. 2014) so make sure to update all your WordPress websites too.
4. Conclusion: If You Are Vulnerable
There is also a web-based test at http://filippo.io/Heartbleed/ where you can check if you are vulnerable. Just type in your website address, and that’s it.
Read more: OpenSSL “heart bleed” bug live blog.
Imagine for looking for legit work-from-home opportunities and finding THIS when you go inside… WOW
Yes, the raw, sizzling beauty of passive income stream online. So click here now. Sometimes ‘later’ becomes ‘never ‘.






 ARE YOU looking for ways to create a legit passive income online?
ARE YOU looking for ways to create a legit passive income online?